Cyber Threats: A Comprehensive Guide to Understanding and Mitigation
 Advanced Health Smartwatch for Women Men with Real-Time Monitoring of Heart rate
Advanced Health Smartwatch for Women Men with Real-Time Monitoring of Heart rate
In today’s interconnected world, cyber threats pose a significant risk to individuals, organizations, and governments alike. Understanding the various forms of cyber threats and implementing effective mitigation strategies is crucial for safeguarding digital assets and ensuring cybersecurity.
Malware
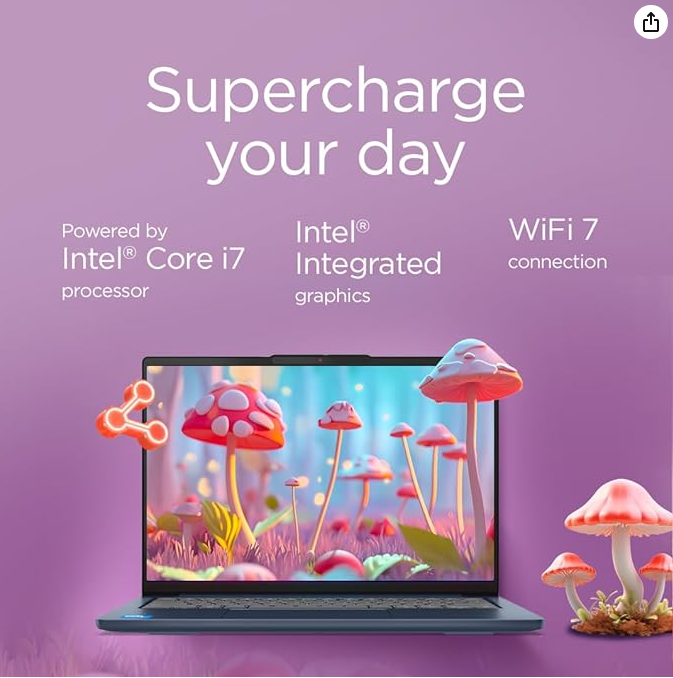 Lenovo IdeaPad Slim 5 | 14 inch WUXGA Laptop | Intel Core i7-13620H | 24 GB RAM | 1 TB SSD | Windows 11 Home | Cosmic Blue
Lenovo IdeaPad Slim 5 | 14 inch WUXGA Laptop | Intel Core i7-13620H | 24 GB RAM | 1 TB SSD | Windows 11 Home | Cosmic Blue
Malware refers to malicious software that infiltrates computer systems and performs unauthorized actions. Common types include:
Viruses
- Replicate themselves and spread through networks, infecting devices and damaging data.
- Examples: WannaCry ransomware, Stuxnet
Spyware
- Monitors and steals sensitive information, such as passwords and financial data.
- Examples: Zeus Trojan, SpyEye
Adware
- Displays unwanted advertisements and can track user activity for data collection.
- Examples: Superfish, Crossrider
Phishing
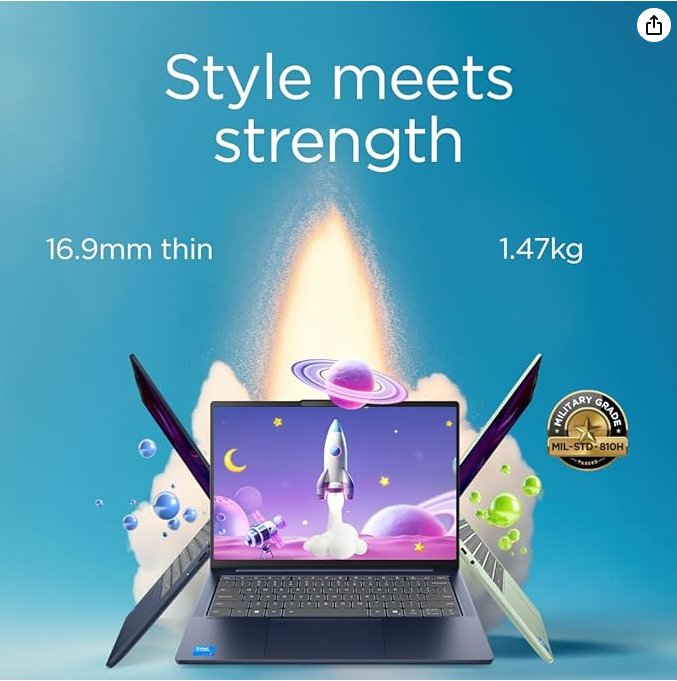 Lenovo IdeaPad Slim 5 | 14 inch WUXGA Laptop | Intel Core i7-13620H | 24 GB RAM | 1 TB SSD | Windows 11 Home | Cosmic Blue
Lenovo IdeaPad Slim 5 | 14 inch WUXGA Laptop | Intel Core i7-13620H | 24 GB RAM | 1 TB SSD | Windows 11 Home | Cosmic Blue
Phishing scams attempt to obtain sensitive information, such as login credentials or financial details, by imitating legitimate websites or emails.
- Uses deceptive emails, text messages, or phone calls that appear to come from trusted sources.
- Examples: Spear phishing targeting specific individuals or organizations
Hacking
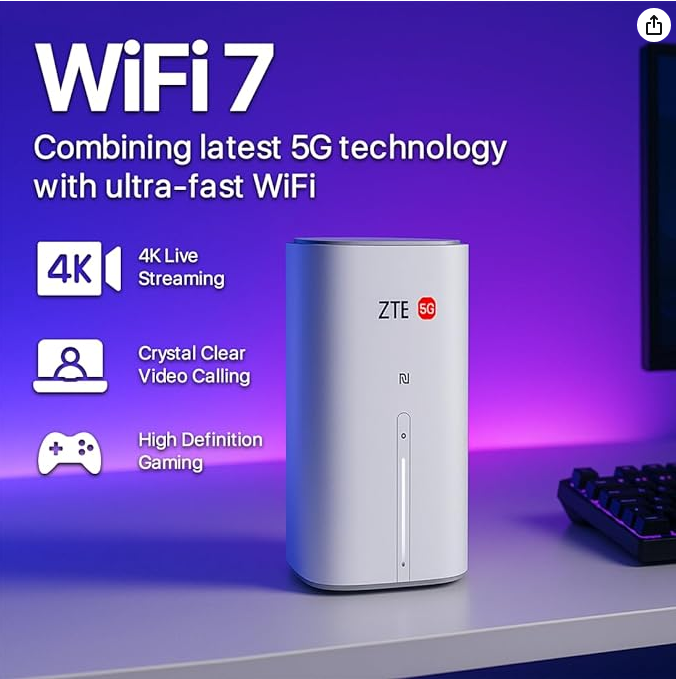 ZTE G5 WiFi 7 5G Router, 3600 Mbps Ultra Fast Home & Office Internet, SIM Slot Unlocked, Dual Band, Connect 128 Devices, 2.5 GbE Port, Smart Antenna – Future Ready WiFi 7
ZTE G5 WiFi 7 5G Router, 3600 Mbps Ultra Fast Home & Office Internet, SIM Slot Unlocked, Dual Band, Connect 128 Devices, 2.5 GbE Port, Smart Antenna – Future Ready WiFi 7
Hacking involves unauthorized access to computer systems, networks, or data. Common methods include:
Brute Force Attacks
- Repeatedly trying different combinations of characters to guess passwords or encryption keys.
- Examples: Remote Desktop Protocol (RDP) brute force attacks
SQL Injection
- Exploiting vulnerabilities in web applications to execute malicious SQL commands.
- Examples: Breaches of e-commerce websites or online banking systems
Social Engineering
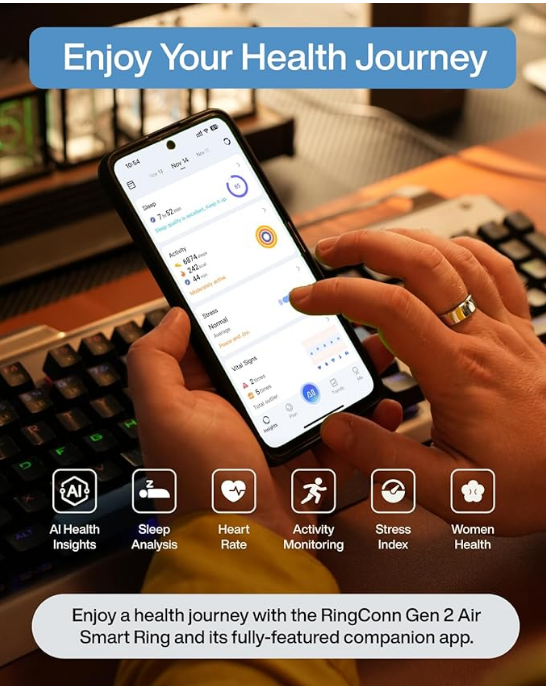 RingConn Gen 2 Air, Ultra-Thin AI Smart Ring, Size First with Sizing Kit, 10-Day Battery Life, Sleep/Heart Rate/Stress/Fitness Tracker, Compatible with Android & iOS - Size 10, Dune Gold
RingConn Gen 2 Air, Ultra-Thin AI Smart Ring, Size First with Sizing Kit, 10-Day Battery Life, Sleep/Heart Rate/Stress/Fitness Tracker, Compatible with Android & iOS - Size 10, Dune Gold
Social engineering techniques rely on human manipulation to gain access to information or systems.
- Preys on human trust and willingness to help.
- Examples: Vishing (phone scams) or pretexting (creating a fake scenario to request sensitive information)
Mitigation Strategies
Network Security
- Firewalls, Intrusion Detection and Prevention Systems (IDS/IPS)
- Monitor and block unauthorized access to networks.
Software Updates
- Keep software, operating systems, and applications up-to-date to patch vulnerabilities.
- Automatic updates ensure timely protection.
Password Management
- Create strong passwords, use two-factor authentication, and avoid reusing passwords across accounts.
- Password managers simplify management and enhance security.
User Education
- Train employees and users on cybersecurity best practices.
- Awareness campaigns help identify and prevent threats.
Data Backup
- Regular data backups ensure recovery in case of data breaches or ransomware attacks.
- Cloud backup services provide secure and off-site storage.
Conclusion
Cyber threats are constantly evolving and pose a significant threat to our digital lives. Understanding the different types of threats and adopting effective mitigation strategies is essential for safeguarding against unauthorized access, data breaches, and financial losses. By staying informed, implementing robust security measures, and fostering a culture of cybersecurity awareness, individuals and organizations can minimize their vulnerability to cyber threats.

