Cyber Threats: A Growing Concern in the Digital Age
 Advanced Health Smartwatch for Women Men with Real-Time Monitoring of Heart rate
Advanced Health Smartwatch for Women Men with Real-Time Monitoring of Heart rate
Cyber threats have become increasingly prevalent in the digital world, posing significant risks to individuals, businesses, and governments. Understanding the different types of cyber threats and implementing effective measures is crucial for mitigating these risks.
Types of Cyber Threats
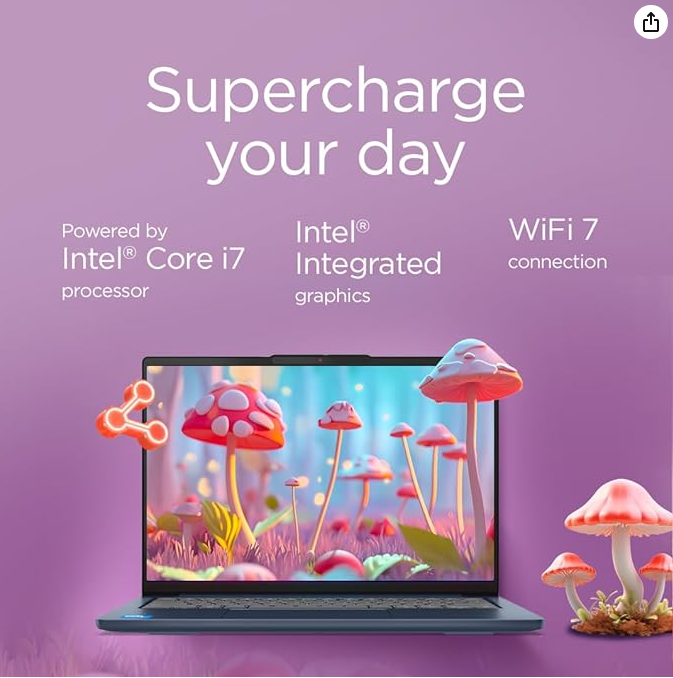 Lenovo IdeaPad Slim 5 | 14 inch WUXGA Laptop | Intel Core i7-13620H | 24 GB RAM | 1 TB SSD | Windows 11 Home | Cosmic Blue
Lenovo IdeaPad Slim 5 | 14 inch WUXGA Laptop | Intel Core i7-13620H | 24 GB RAM | 1 TB SSD | Windows 11 Home | Cosmic Blue
Malware
- Viruses: Malicious software that attaches itself to legitimate programs or files, infecting systems and damaging data.
- Trojans: Camouflaged as legitimate software, they allow attackers to gain unauthorized access to systems.
- Ransomware: Encrypts files and demands payment to restore access, targeting businesses and individuals alike.
Phishing Attacks
- Email Phishing: Fake emails resembling legitimate sources, tricking users into revealing sensitive information or clicking malicious links.
- Smishing: Phishing attacks carried out via SMS text messages, targeting mobile devices.
- Vishing: Voice-based phishing attacks where criminals call potential victims, impersonating customer support or authorities.
Social Engineering
- Pretexting: Impersonating a trusted individual or organization to manipulate victims into providing sensitive information.
- Spear Phishing: Targeted phishing attacks specifically designed to deceive specific individuals or organizations.
- Baiting: Luring victims with attractive offers or promises, leading them to download malicious software or provide sensitive data.
Security Breaches
- Data Breaches: Unauthorized access or theft of sensitive data, such as personal information, financial records, or trade secrets.
- Network Attacks: Exploiting network vulnerabilities to gain unauthorized access to systems or disrupt operations.
- DDoS Attacks: Overwhelming a website or network with traffic, causing it to become inaccessible.
Cyber Espionage
- State-sponsored Hacking: Governments or intelligence agencies engaging in cyber espionage to gather sensitive information or disrupt operations of other nations.
- Corporate Espionage: Businesses targeting competitors to steal trade secrets or gain a competitive advantage.
- Hacktivism: Individuals or groups hacking into systems to send political messages or cause damage.
Conclusion
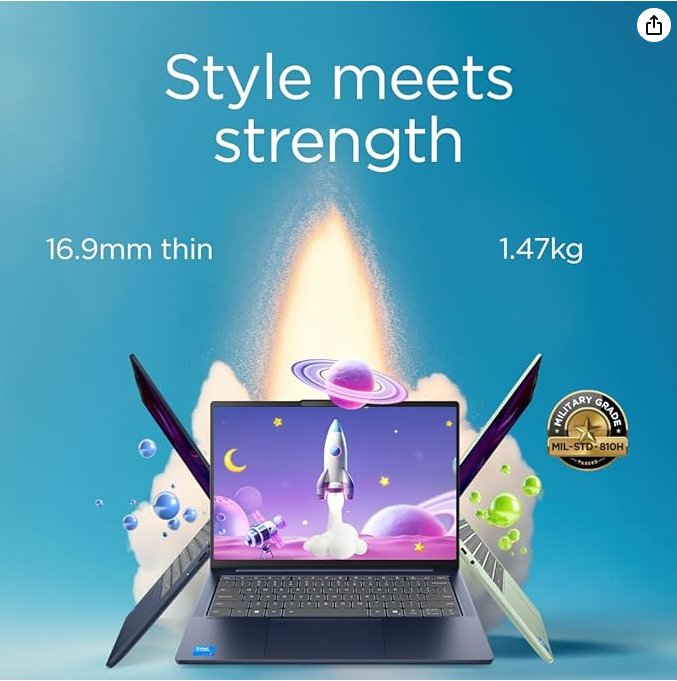 Lenovo IdeaPad Slim 5 | 14 inch WUXGA Laptop | Intel Core i7-13620H | 24 GB RAM | 1 TB SSD | Windows 11 Home | Cosmic Blue
Lenovo IdeaPad Slim 5 | 14 inch WUXGA Laptop | Intel Core i7-13620H | 24 GB RAM | 1 TB SSD | Windows 11 Home | Cosmic Blue
Cyber threats are a constant and evolving threat that require ongoing vigilance and proactive measures. By understanding the different types of threats, implementing robust cybersecurity strategies, and staying informed about the latest threats, individuals and organizations can mitigate risks and protect their digital assets. Regular updates to software and systems, employee education, and collaboration with cybersecurity experts are crucial for maintaining a strong defense against cyber threats.

